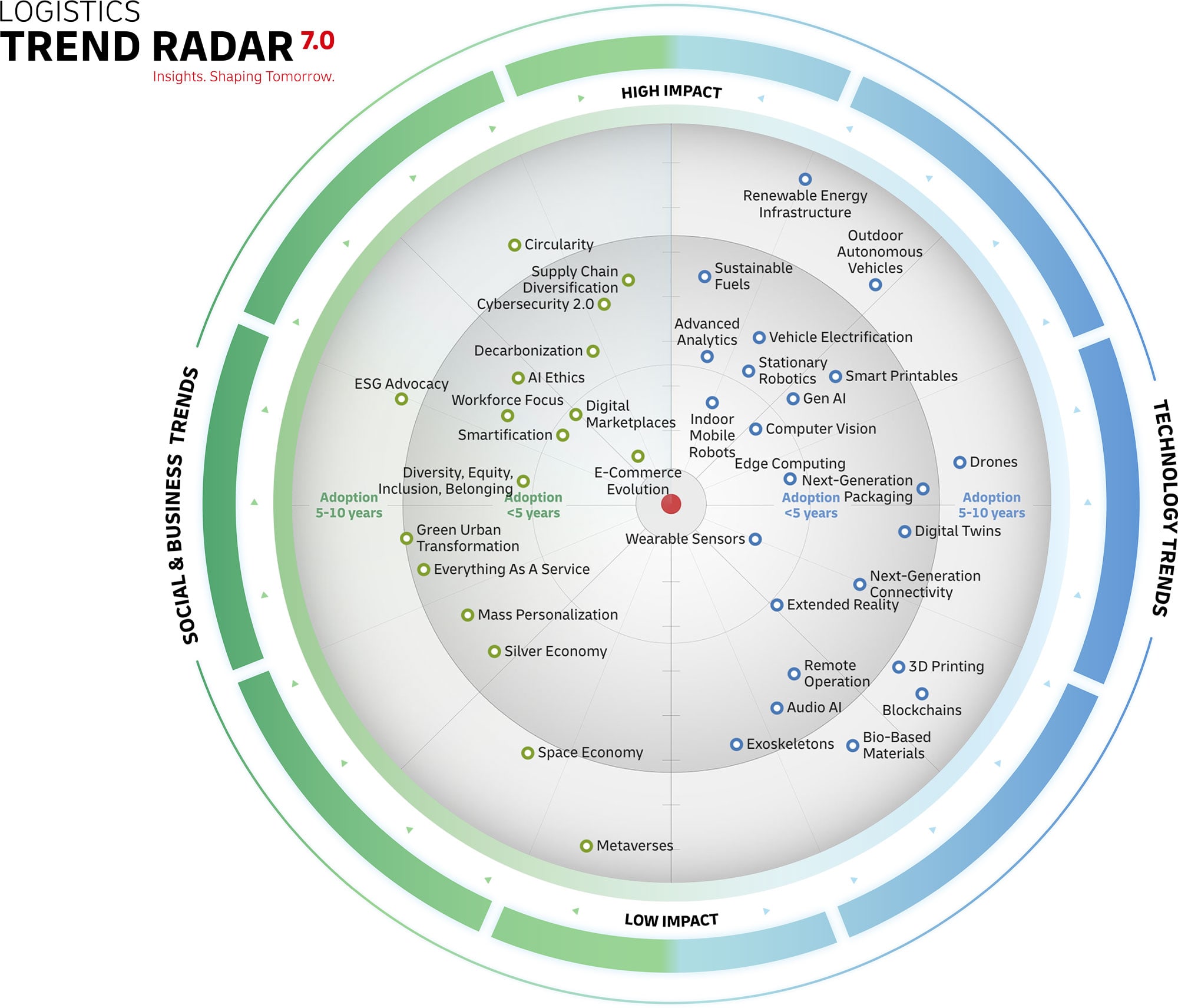
The trend of Cybersecurity 2.0 encompasses the next generation of solutions, processes, and standard operating rules and regulations that leverage artificial intelligence (AI) and other advanced technologies and ways of working against cyberthreats. It involves protection, detection, and response tools that not only prevent attacks but also actively predict and autonomously detect threats and respond to attacks.
Due to their critical role, logistics networks are a prime target for cyberattacks. Across the entire supply chain, technological advances in generative AI, quantum computing, and more represent an increasing challenge to traditional protection and encryption methods. Attackers seek to compromise the weakest link in supply chains, which could be a software supplier or hardware manufacturer whose products are used within the infrastructure. Meanwhile, increased usage of digital infrastructure, pervasive connectivity, and convergence expose previously isolated assets in operations (operational technology).
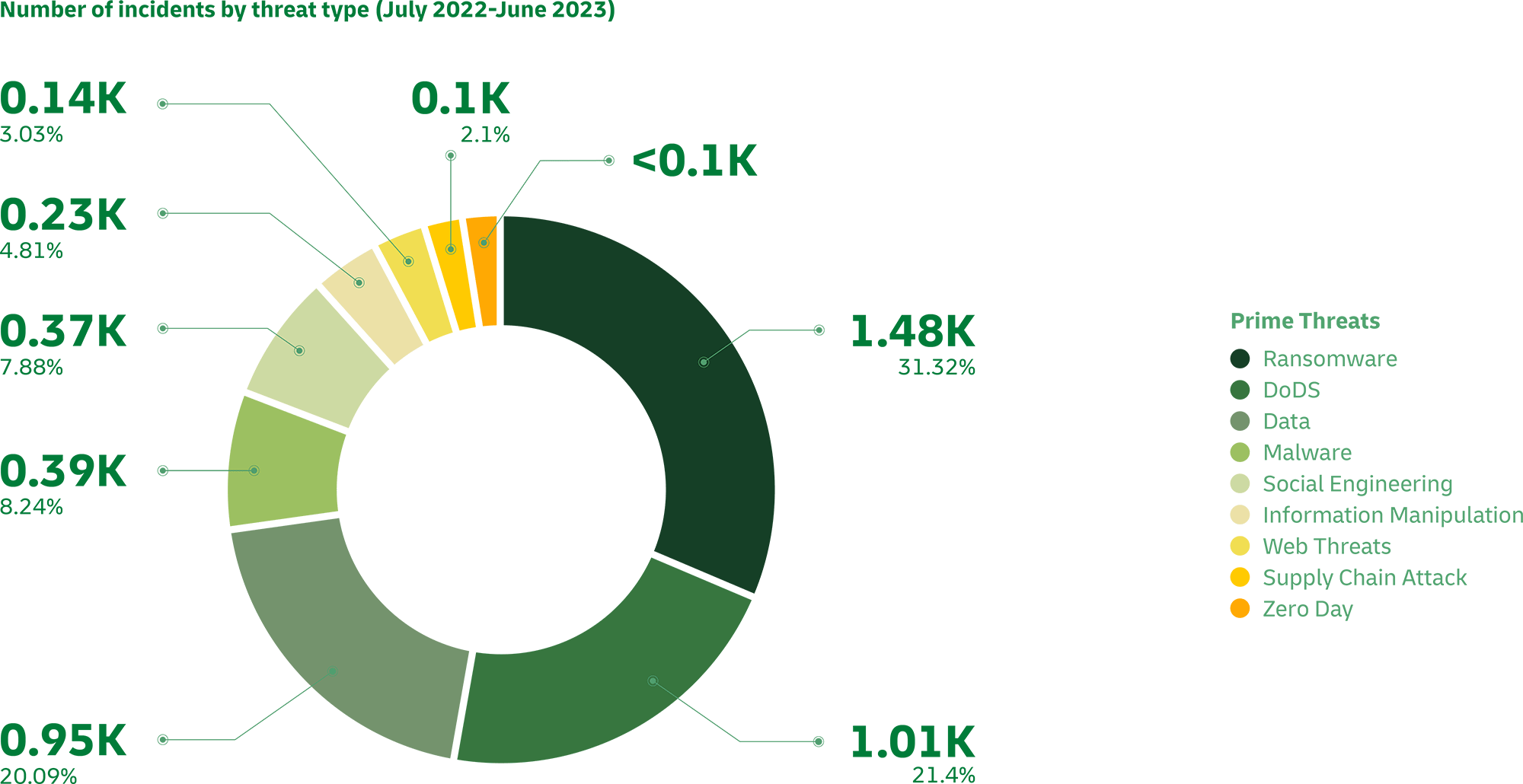
Not only cybersecurity teams but also every logistics professional must be vigilant. Major risks include ransomware, AI attacks, malware, denial of service, information manipulation and interference, and attempts to convince employees to share confidential information (known as social engineering). Moreover, increasingly sophisticated hacking makes it difficult to detect the launching of “dark” services such as FraudGPT and WormGPT.
Cyberattacks can significantly impact logistics organizations. Importantly, such an impact can reverberate throughout the entire supply chain, creating a ripple effect that can cause up to 26 times the loss for a company’s business ecosystem. For this reason, the trend of Cybersecurity 2.0 will undoubtedly play a pivotal role in ensuring the resilience and security of organizations in all sectors.
Here at DHL, we recognize the transportation sector is a prime target for ransomware due to its critical role in the supply chain. As logistics operations are heavily driven by digital applications and integration, enabling global reach within the supply chain ecosystem, any threat to these core tools could devastate the entire ecosystem and flow of goods.
Increases in vast data sets from the rise in Internet of Things (IoT) implementations provide attackers with a ready supply of data to sell or exploit. And just as AI and automation are helping logistics companies be more efficient, cybercriminals are using these capabilities in attacks which are increasingly hard to detect and manage.
As risks increase in the supply chain, the growing demand for skilled cybersecurity professionals outpaces the supply of qualified candidates.